What Are CMMC Assessments?
CMMC assessments give the Department of Defense assurance that sensitive information, specifically CUI and FCI, shared with the defense industrial base (DIB) is secure. The Cybersecurity Maturity Model Certification (CMMC) 2.0 program increases accountability and streamlines the cybersecurity review process.
There are three Maturity levels for CMMC Assessments:
- Maturity Level 1: Self-Assessment or Third-Party Assessor Accepted
- Maturity Level 2: Third-Party Assessor (C3PAO) Required
- Maturity Level 3: Government Assessors Required
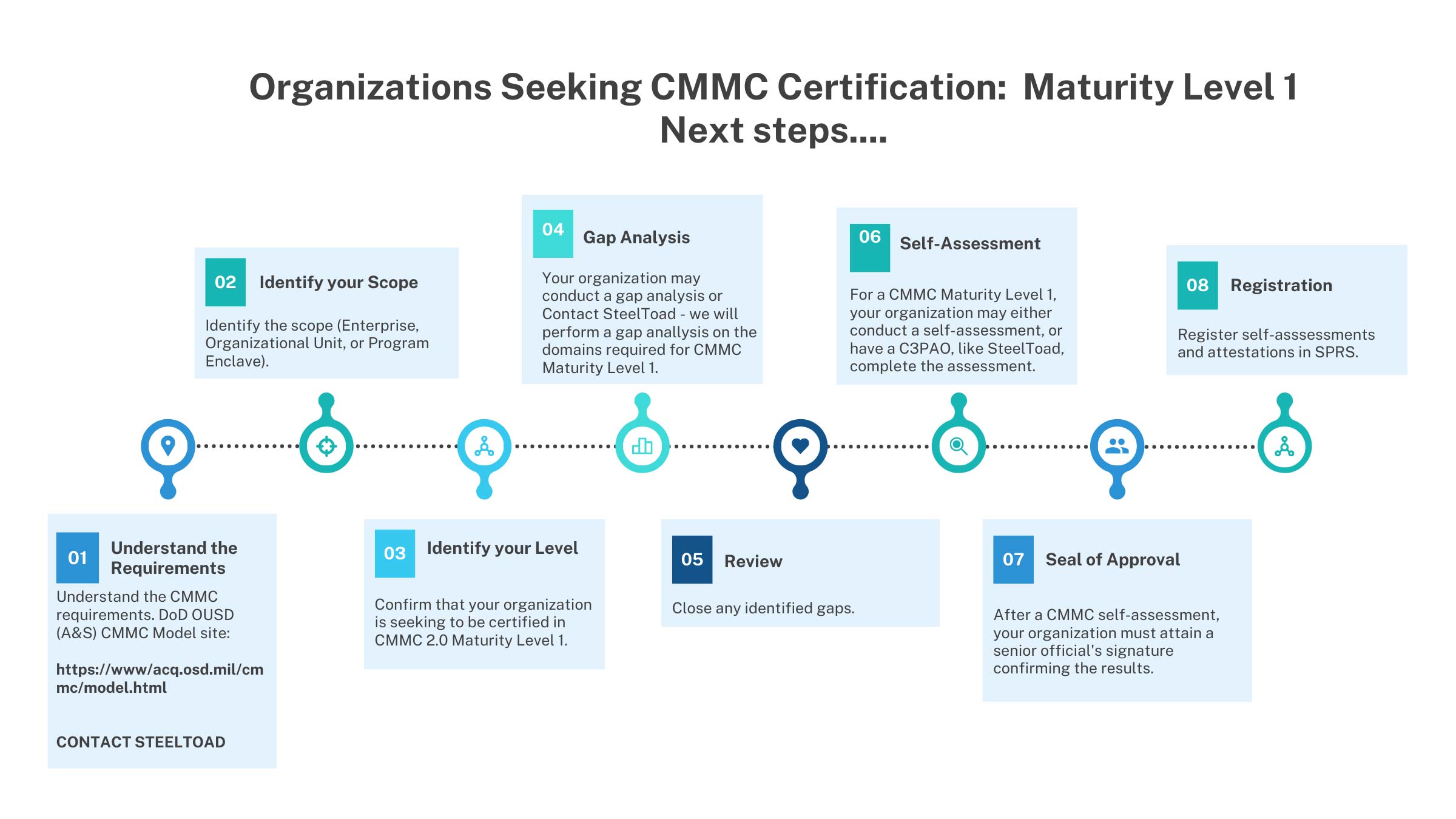
CMMC 2.0 Self Assessments
One of the modifications brought about by CMMC 2.0 was the approval for some organizations to conduct a self-assessment to attain Level 1. This pertains to organizations working with FCI alone or managing CUI that is not important to national security. This was a welcome answer to the concern raised by smaller businesses about the cost of having to achieve CMMC certification when the organizations had limited interaction with FCI or CUI.
Self-Assessment to obtain CMMC Level 1 will necessitate a review of the organization’s infrastructure, against only 17 practices within the CMMC 2.0. The self-assessment for CMMC 2.0, Maturity Level 1 must be completed annually, and the results must be documented and posted on the SPRS website. To maintain the process’s integrity, senior management must sign off on the self-assessment.
To lead an organization through a self-assessment, DOD has published CMMC Assessment Guides. The CMMC Self-Assessment Guide will provide the following information for your organization:
- Define terms and CMMC practices
- Defines the CMMC Assessment methodology
- Describes and defines “Objects”, “Criteria”, “Processes”, “Findings”
- Provides detailed information on self-assessment guidance and requirements.
- Describes how self-assessment relates to the CMMC 2.0 practices.
- Defines how a CMMC 2.0 model assessment focuses on data, not the size or structure of an organization.
- Defines the scope of the self-assessment and provides additional resources for the organization.
A self-assessment for CMMC Level 1 must encompass the following six domains and (17 practices): The domains include:
- Access Control
- Identification and Authentication
- Media Protection
- Physical Protection
- System and Communication Protection
- System and Information Integrity
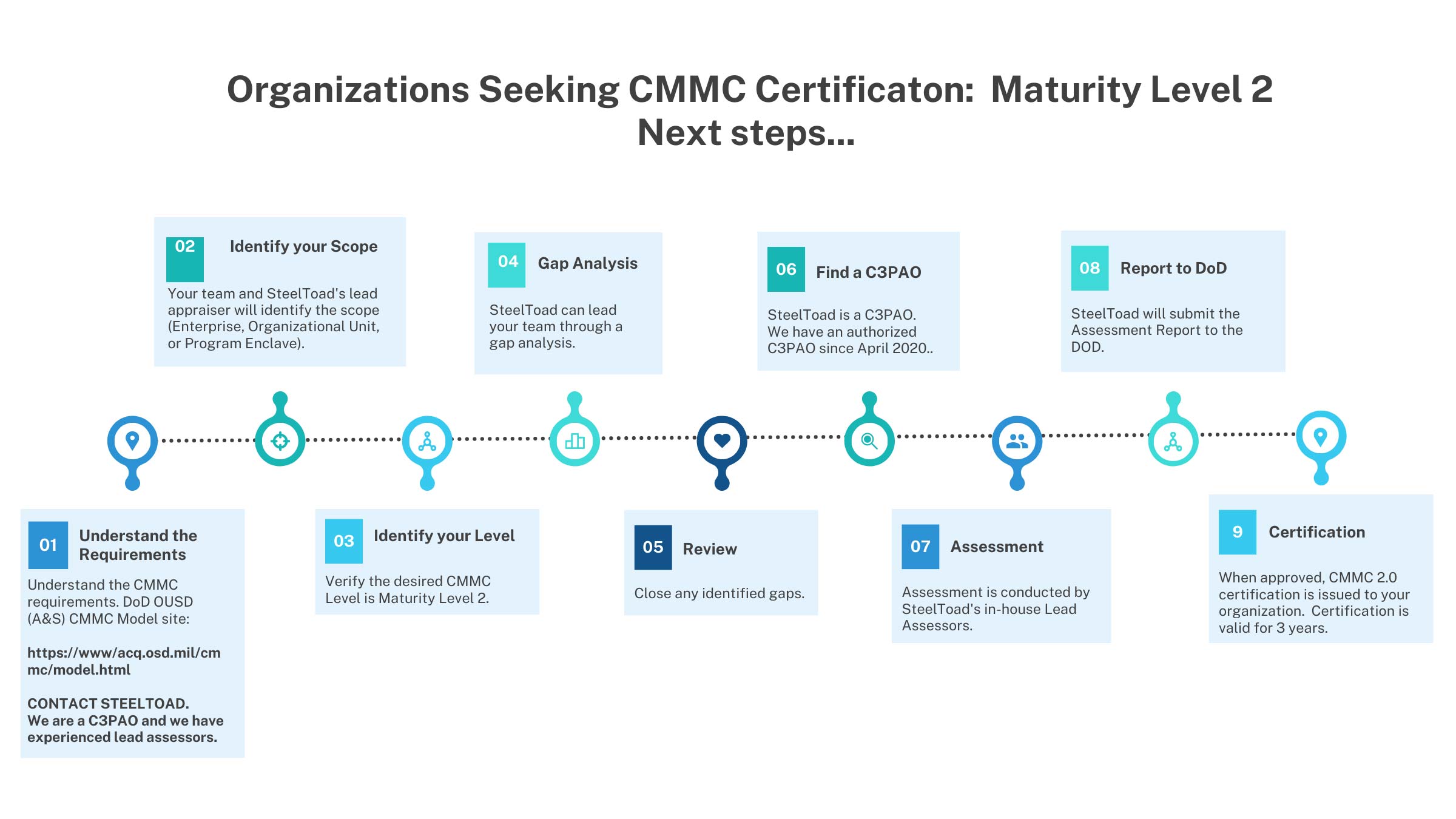
CMMC 2.0 Third-Party Assessments
CMMC Model, Maturity Level 2 Assessments must be conducted by CMMC authorized Third Party Organizations (C3PAOs). SteelToad is an authorized C3PAO to conduct CMMC 2.0 assessments, to determine whether an organization’s security practices are being applied to meet the cybersecurity standards of the CMMC 2.0 Model.
Organizations aiming to achieve the CMMC 2.0 Model Maturity Level 2, will contract directly with SteelToad, a CMMC C3PAO. A SteelToad lead appraiser must work under the authority of an authorized C3PAO, such as SteelToad to conduct the assessment. SteelToad has a team of lead appraisers, who are employed with our company and have completed several CMMC assessments with DoD under the DOD Joint Surveillance Program.
Organizations seeking certification (OSCs) may work toward CMMC certification for a host unit, system, department, or enclave within the organization. The scope of the assessment, determined by the lead assessor and the OSC, will focus solely on the areas within the organization that stores, processes, or transmits CUI and FCI. The CMMC Assessment Scope will inventory all the IT assets that will be assessed in the organization’s environment.
SteelToad follows the CMMC Assessment Process (The CAP), the official roadmap required to guide C3PAOs and Lead Assessors. The CAP was created to give a method for maintaining consistency throughout CMMC assessments to establish consistent expectations for Organizations Seeking Certifications, C3PAOs, Lead Assessors, and all entities performing assessments in the CMMC Ecosystem.
When performing a CMMC assessment, SteelToad uses the CMMC Assessment Process (CAP) document which defines four CMMC assessment phases:
- Phase 1: Develop an assessment plan
- Phase 2: Make an assessment
- Phase 3: Provide an assessment report
- Phase 4: Assess and close out POA&Ms.
The CMMC Assessment Process (CAP) states its objectives for every CMMC Assessment:
- Ensure the highest level of quality, accuracy, and fidelity in C3PAO CMMC Assessments
- Maximize consistency by making sure differences in assessment results and outcomes between C3PAOs and Assessors are consistent
- Provide effective and efficient cybersecurity assessments, executed consistently and accurately, that improve the DIB’s cybersecurity defensive posture.
SteelToad clients expect our Lead Appraisers to follow the CAP guidelines to achieve the highest integrity of the Assessment Process.
- A CMMC Level 2 assessment will encompass the following fourteen security domains:
- Access Control: Control who can access your network and systems.
- Audit & Accountability: Ensure logs are created and checked frequently.
- Awareness & Training: Provide proper training to your employees.
- Configuration Management: Update baselines and other configurations regularly.
- Identification & Authentication: Know who is requesting access and authenticate appropriately.
- Incidence Response: Know how to recover when an incident occurs.
- Maintenance: Make sure your systems are up to date and patched.
- Media Protection: Protect media from theft and loss.
- Personnel Security: Reduce insider risks to your environment.
- Physical Protection: Use physical protection mechanisms to prevent access to physical devices.
- Risk Assessment: Use a process for identifying and managing risk.
- Security Assessment: Have your security posture independently verified.
- Systems and Communications Protection: Oversee security tools and processes related to system security.
- Systems and Information Integrity: Identify and prevent malicious content from entering the system.
Ask SteelToad About It
We are currently conducting CMMC Voluntary Assessments under the Joint Surveillance Program with DoD.
What does SteelToad need from my organization for a CMMC Assessment?
The Assessment Methodology defines how SteelToad’s lead appraisers will conduct the CMMC 2.0 assessment. SteelToad Lead Appraisers will verify and validate that the organization is implementing the CMMC Level 2 110 practices using three assessment methods, examination of artifacts, interviews of personnel, and testing of security controls.
Examination methods include the review of documents, activities, processes, and activities. A lead appraiser may review reports, plans, training course materials, policy documents diagrams, or flow charts. The organization is providing information, in varied formats, to show how the processes within the organization are meeting the security process controls. The examination requires that documents be in their final format. Draft or pending documents may not be utilized as evidence in an assessment.
Interview methods will be planned so the lead appraiser may discover and understand how security practices are implemented. The lead appraiser will be able to ascertain whether there is appropriate implementation, training, resources, and process in place to meet the needed standard through question-and-answer sessions and discussions.
Testing methods provide an understanding of the security controls in operation within an organization. The purpose of testing a security practice is to compare the actual behavior to the expected behavior. Results from the test are used to determine whether a security safeguard exists, is functional, is correct, is complete, and has the potential to improve over time and institutionalization. For a test/demonstration to be accepted as Evidence in an Assessment, it must pass its requirements and criteria while being observed by the Assessment Team
The CAP states:
The organization does not have to use all three assessment methods (Examine, Interview, Test) for every practice. Instead, [Certified Assessors] are able to determine the level of effort and level of assurance required for an Assessment (e.g., which Assessment methods and Assessment objects are deemed to be the most useful in obtaining the desired results). Assessment objectives are determined by considering how the organization can achieve them most cost-effectively and with enough confidence to support a conclusion that the CUI requirements have been met.
SteelToad is an authorized CMMC C3PAO with CMMC Assessors available to assist your team in conducting assessments against the standards set forth in NIST 800-171, and the CMMC Model.
Next Steps:
What are the CMMC Domains in a CMMC Assessment?
The CMMC Framework comprises fourteen cybersecurity categories, each with a set of associated practices and objectives in a tiered structure emphasizing the commitment to protect CUI and FCI. The CMMC Model domains are based on the NIST 800-171 cybersecurity control requirements and are categorized as domain, practice, and assessment objectives.
Domain
The tiered and focused structure of CMMC begins with the Domain which defines the category of security.
Practice
The next tier is Practice. A Practice is an activity or set of activities that are completed to meet the defined CMMC objectives. Within an organization, Practice is a routine activity that an organization completes to demonstrate cybersecurity capabilities.
Assessment Objectives
The next level is the specific set of objectives that must be met to complete a Practice. If all Assessment Objectives are completed, the practice will be marked as “MET”.
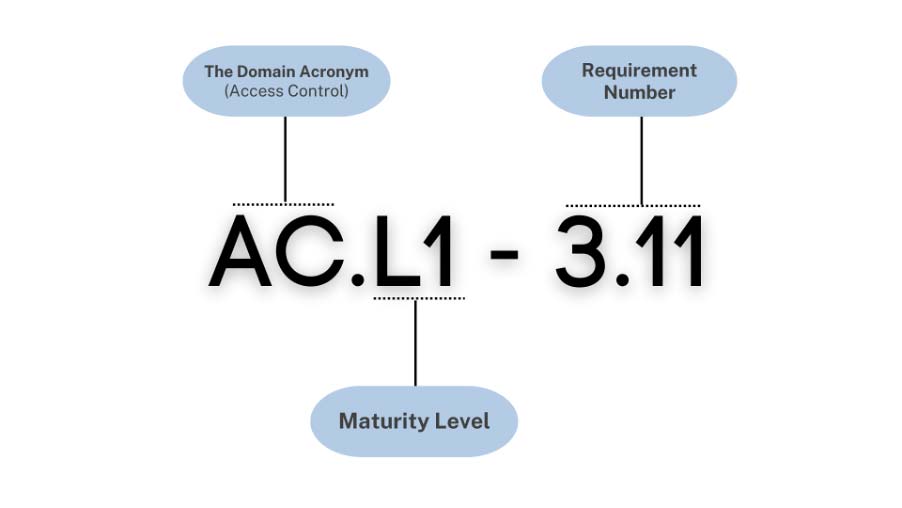
The Assessment Model numbering system is important for a proper understanding of each Practice Statement. The practice numbering system includes the Domain, Level & Requirement.
For example, AC.L1-3.1.1 would indicate that the Domain is Access Control, the Maturity Level is ML 1 and the Requirement Number is Requirement 3.1.1. Also, it is important to note that the Practice Numbers are inherited from the original NIST SP source, such as NIST SP 800-171 Rev 2 and NIST SP 800-172.
Practices accumulate throughout the levels in the CMMC Model, as it is defined as a Maturity Level Model. The designation “Maturity” indicates that as practices are added, an organization builds on its “Maturity Level” for that practice. For example, Level 1 contains 17 practices considered to be ‘Foundational.” At Level 2, there are 110 practices considered to be “Advanced.” Amongst those 110 practices are the original 17 practices from Level 1. Level 3 encompasses all 110 practices from Levels 1 & 2 as well as the additional practices from NIST 800-171. The cumulation of all practices names Level 3 as “Expert.”
CMMC Model Domains:
- Access Control: Manage who has access to your networks and systems.
- Audit & Accountability: Ensure logs are created and checked frequently.
- Awareness & Training: Ensure your employees are trained correctly.
- Configuration Management: Ensure your baselines and other configurations are kept up to date.
- Identification & Authentication: Know who is requesting access and authenticate appropriately.
- Incidence Response: Know how to recover when an incident occurs.
- Maintenance: Make sure your systems are up to date and patched.
- Media Protection: Ensure media is protected against theft or loss.
- Personnel Security: Manage risks to your environment by insiders.
- Physical Protection: Use physical protection mechanisms to prevent access to physical devices.
- Risk Assessment: Use a process for identifying and managing risk.
- Security Assessment: Have your security posture independently verified.
- Systems and Communications Protection: Manage security tools and processes related to system security.
- Systems and Information Integrity: Monitor and protect the information system against malicious content.
CMMC Certification Cost
In order to determine the CMMC assessment costs, several factors must be considered, such as the level of the CMMC, the complexity of the DIB’s unclassified network for the certification boundary, and commercial forces.
SteelToad should meet with your team, (the Organization Seeking Certification) briefly, to discuss the assessment framing and the CMMC Assessment Process (The CMMC AB’s assessment process for all Certified CMMC Assessors to follow). The conversation between SteelToad and your business will aid SteelToad in defining the scope and offering your business a fixed price quotation and methodology for the CMMC services requested.
These CAP elements, once discussed, help determine the cost estimate of the assessment:
- The location(s) of the assessment, as well as what aspects and activities will be undertaken virtually; 15 practices will be analyzed physically.
- Identifying OSC staff to provide evidence for the assessment.
- OSC’s CMMC Assessment Scope
- The relevant documentation of the OSC’s information and technology staff(s) as well as its information security staff(s)
Please give SteelToad a call to discuss your organization’s scope, and to receive an estimated cost for the assessment.
Will The Results Of My Assessment Be Public? Will The DoD See My Results?
The DoD will have access to the results of an organization’s CMMC 2.0 assessment and the final report once CMMC 2.0 has been implemented. DoD will keep all evaluation findings in the Supplier Performance Risk System (SPRS). The CMMC Enterprise Mission Assurance Support Services (eMASS) database will be used to store CMMC certifications along with the information related to third-party assessments. There will be no public release of the results of the CMMC assessment.
Frequently Asked Questions (FAQs)
A CMMC assessment evaluates an organization’s cybersecurity practices and processes to ensure the secure handling of sensitive Department of Defense (DoD) information, precisely Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). The CMMC 2.0 program offers a streamlined review process for the Defense Industrial Base (DIB).
To become a certified CMMC Assessor (CCA), one needs to complete the CMMC Certified Professional (CCP course), pass the exam, and then successfully take the CMMC Certified Assessor Training course, and pass the CMMC CCA exam to achieve necessary certifications, and be affiliated with a CMMC Third-Party Assessor Organization (C3PAO). The certification process ensures the assessor is well-versed with the standards and practices outlined in the CMMC 2.0 model.
SteelToad’s CMMC Assessment involves evaluating an organization’s cybersecurity practices against the standards set in the CMMC 2.0 Model. This includes developing an assessment plan, conducting the assessment, providing an assessment report, and assessing and closing out any Plan of Action and milestones (POA&Ms). SteelToad’s assessment follows the official CMMC Assessment Process (CAP).
The duration of SteelToad’s CMMC assessment can vary based on the organization’s size and complexity, the assessment’s scope, and the specific CMMC level being pursued. It is advisable to consult directly with SteelToad, and after learning the requirements in more detail, we will be able to provide a more precise timeline.
The cost of SteelToad’s CMMC assessment depends on several factors, including the CMMC level being pursued, the size and complexity of the organization, and the scope and specific requirements of the assessment. For a detailed cost estimate, it is recommended to contact SteelToad directly at team@steeltoad.com or (833) 333-TOAD (8623).