800-53. NIST SP 800-53
800-171. NIST SP 800-171
NIST CSF.
RMF. Risk Management Framework
HVA. High Availability Assets
A&A. Assessment and Authorization
CRR. Cyber Resilience Review
EDM. External Dependencies Management
HIPAA.

SteelToad’s Cyber Assessments provide an excellent method of evaluating and verifying that a government agency’s security and privacy goals are satisfied. Our team of assessors examines an organization’s infrastructure against a specific security framework to determine the consistency of best practices in accomplishing the organization’s goals. Cybersecurity has emerged as one of the most critical challenges confronting the federal government and its partner entities. As more information is shared, there is a greater need for security and privacy safeguards. However, even the best-laid plans are pointless unless organizations adhere to the standards they develop to avoid cybersecurity risk and breach. The importance of implementing cybersecurity policies, procedures, and behaviors is paramount.
With our knowledge of multiple cybersecurity frameworks, SteelToad is at the forefront of providing excellent organized assessments. Assessments should occur often, throughout the lifecycle of a system. Please contact us to discuss your organization’s IT environment and assessment requirements.
NIST 800-53 Assessment
The need to consistently and thoroughly protect an organization’s systems from cyberattacks has become an essential requirement. In order to make risk avoidance a routine and consistent practice, it is critical that organizations approach risk avoidance in a proactive manner.
Ten years ago, NIST was given the responsibility, by Executive Order 13636, to establish requirements for a cybersecurity framework, in order to address the issues facing federal infrastructure security due to the increase in cybersecurity breaches. In response to this Executive Order, NIST published multiple cybersecurity Special publications along with related industry-specific Special Publications to detail how these cybersecurity standards address a particular industrial sector and relate to that industry.
With the issuance of the Special Publication “800 series”, which was set up to define cybersecurity standards, frameworks, risk assessments and security controls, federal entities are given guidance on required security controls for the IT systems.
By conducting a NIST 800-53 or a NIST 800-171 evaluation, organizations will be able to identify the current state of their processes against security controls defined by the National Institute of Standards and Technology. With the assessment results, organizations can identify strengths and weaknesses, and then work to correct gaps and strengthen their defenses to better meet their cyber objectives.
All federal government information systems must be able to demonstrate that the systems they employ to carry out their missions meet each of the security measures outlined in NIST SP 800-53 as a minimum.
The requirement was established as a mandate from both the Office of Management and Budget (Circular A-130) and the Federal Information Security Modernization Act (FISMA) to ensure that federal systems protect the data within its IT infrastructure. This is a current requirement for all federal government systems.
SteelToad’s NIST 800-53 Cybersecurity Assessment is modeled from the NIST Special Publication 800-53A, Assessing Security and Privacy Controls in Federal Information Systems and Organizations, and enhanced by our experience in performing best processes assessments in cybersecurity, ISO and CMMI, and CMMC.
Adherence to the NIST 800-53 security control families, helps organizations limit their IT risk and align their IT infrastructure to safeguard against the barrage of cybersecurity attacks. Any organization that uses information systems that process, store, and transmit data, will benefit by aligning with these protocols. The National Institute of Standards and Technology developed the NIST SP 800-53 set of 24 security control families with input from associated cybersecurity organizations and professionals, in an effort to secure the federal government’s information and limit risk to its IT infrastructure.
NIST 800-53 Security Controls are the administrative, technical, and physical processes and safeguards. There is a structure to how the 800-53 security controls are communicated; NIST presents a format to show each security control, its definition, a brief explanation, related and relevant references. In order to give users clarity, sets of security controls are organized into security control families.
There are 24 Security Control Families in NIST 800-53. Families are made up of Base Controls and Enhanced Controls. Base Controls provide the minimum standard in the family of controls, and Enhanced Controls define extra security features and capabilities that “improve the base control”. An Enhanced control expands on a base control by adding functionality to it, but it does not affect the basic control itself.
SteelToad’s NIST 800-53 Cybersecurity Assessment is modeled from the NIST Special Publication 800-53A, Assessing Security and Privacy Controls in Federal Information Systems and Organizations, and enhanced by our experience in performing best processes assessments in cybersecurity, ISO and CMMI, and CMMC.
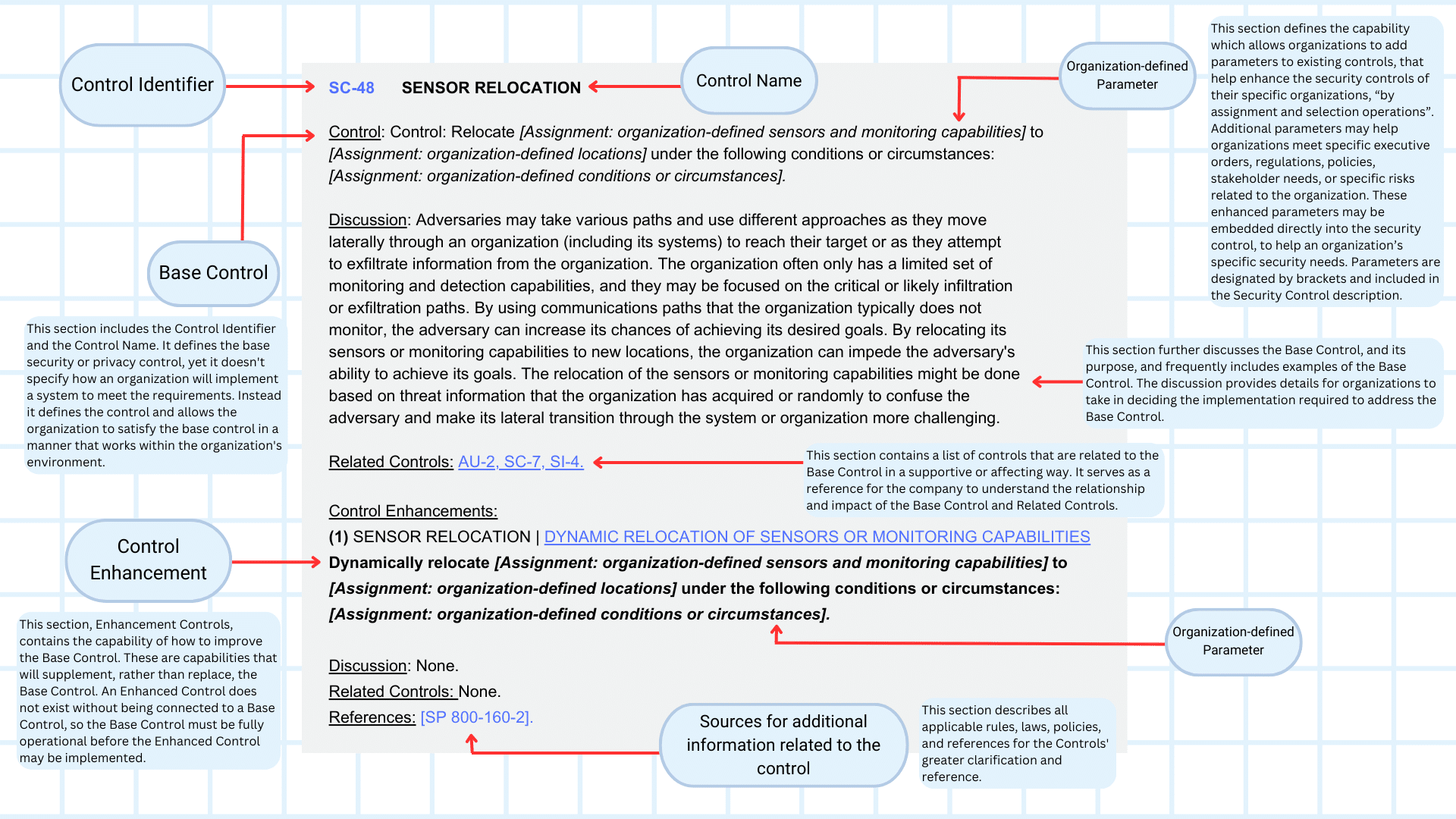
The following is an example of how NIST SP 800-53 communicates its Security Controls.
The NIST SP 800-53 Security Control, communicated in the “template” shown above, includes information, for each of the 24 families of security controls, as follows:
- 800-53 Base Control Section: This section defines the base security or privacy control which is required by organizations. The Base Control does not specify how an organization will implement a system to meet the requirements, instead, it defines the control and allows the organization to satisfy the base control in a manner that works within the organization’s environment.
- 800-53 Discussion Section: This section further discusses the Base Control, and its purpose, and frequently includes examples of the Base Control. The discussion provides details for organizations to take in deciding the implementation required to address the Base Control.
- 800-53 Related Controls Section: This section contains a list of controls that are related to the Base Control in a supportive or affecting way. It serves as a reference for the company to understand the relationship and impact of the Base Control and Related Controls.
- 800-53 Control Enhancements Section: This section, Enhancement Controls, contains the “enhancement” to improve upon the Base Control. These capabilities will supplement, rather than replace, the Base Control. An Enhanced Control does not exist without being connected to a Base Control, so the Base Control must be fully operational before the Enhanced Control may be implemented.
- 800-53 References Section: This section describes all applicable rules, laws, policies, and references for the Controls’ greater clarification and reference.
- 800-53 Organizational Defined Parameters: This section defines the capability which allows organizations to add parameters to existing controls, that help enhance the security controls of their specific organizations, “by assignment and selection operations”. Additional parameters may help organizations meet specific executive orders, regulations, policies, stakeholder needs, or specific risks related to the organization. These enhanced parameters may be embedded directly into the security control, to help an organization’s specific security needs. Parameters are designated by brackets and included in the Security Control description.
NIST 800-171 Assessment
NIST 800-171 was designed to establish standards, for all non-federal organizations handling “Controlled Unclassified Information (CUI)”. Although some data is not considered “classified”, there is a level of data, which is stored, transported, shared and utilized between federal and non-federal systems, that is sensitive, and must be protected.
NIST 800-171 provides a set of standards, for non-federal organizations, to protect unclassified federal data being shared and used between federal and non-federal systems. With and increase in commercial industry and federal government collaboration and an increase in hacking and cybercrime, a gap or breach in a commercial system that is linked to a federal system, is a risk to all organizations and data exponentially.
Executive Order 13556 mandated the establishment and implementation of a federal program for protecting Controlled Unclassified Information. SteelToad’s assessors can help your organization, through an assessment that checks your system’s processes and procedures against the security controls in NIST 800-171 (rev.2).
NIST CSF
The National Institute of Standards and Technology created CSF to improve cybersecurity within critical infrastructure. At the core of SteelToad’s capabilities – our team understands how to leverage our experience in mission-critical technology solution delivery with our expertise in maturity level and cybersecurity assessment services, and helping clients, through asssessment services, to align with NIST CSF. A central benefit of NIST’s CSF framework is its characteristic of flexibility and SteelToad understands how to work with our clients to assess technology environments, and to uncover strengths and weaknesses.
American Association for Laboratory Accreditation (A2LA) approved SteelToad in the following cybersecurity assessment scopes: NIST CSF, DFARS 252.204-7012 and NIST 800-171, Penetration Testing Execution Standard (PTES) and Open Web Application Security Project (OWASP), FISMA NIST 800-53, and HIPAA 45 CFR 164 (Certificate #7300.01).
SteelToad’s expertise in cybersecurity frameworks lends itself to the application and comprehensive approach we use in evaluating our client’s environment, aligning with NIST CSF (Identify, Protect, Detect, Respond and Recover). Let us help align your organization!
More Cyber Assessments, HVA. RMF. A&A. EDM. CRR. HIPAA.
ASSESS.
It is imperative to avoid undue risk, and to fully defined security processes with enough detail that it can be consistently performed by trained and skilled people and is both persistent and habitual.
A comprehensive assessment is a huge checkpoint for decision-makers, stakeholders, and users. To ensure the process is accurate and produces correct results, assessments must be carried out by professionals with expertise, integrity, and experience. SteelToad is this company. SteelToad has completed Cybersecurity & Infrastructure Security Agency (CISA) assessment training programs for the Cyber Resilience Review (CRR), External Dependencies Management (EDM) and the HVA (Non-Tier 1 High Value Assets) assessments.
The CISA-led assessment program goals are to:
Produce a federal, and private sector, workforce of prepared and qualified assessors.
Ensure assessors have the knowledge and skills necessary to conduct assessments according to the CISA standards and methodologies.
Ensure assessment results are of high quality, consistent, and repeatable.
Cyber Resilience Review (CRR)
SteelToad Cyber Resilience Review (CRR) assessments are interview-based assessments to evaluate an organization’s operational resilience and cybersecurity practices. This assessment is derived from the CERT Resilience Management Model (CERT-RMM), a process improvement model developed by Carnegie Mellon University’s Software Engineering Institute for managing operational resilience. Cyber Resilience Review assessments evaluate the maturity of an organization’s capacities and capabilities in performing, planning, managing, measuring, and defining cybersecurity capabilities across the following ten domains:
- Asset Management
- Controls Management
- Configuration and Change Management
- Vulnerability Management
- Incident Management
- Service Continuity Management
- Risk Management
- External Dependency Management
- Training and Awareness
- Situational Awareness
SteelToad has been awarded all five High Availability Cybersecurity (HACS) labor categories on GSA Schedule 47QTCA20D00BS.
SteelToad’s HACS Awarded categories:
- High-Value Asset Assessments
- Risk and Vulnerability Assessment
- Cyber Hunt
- Incident Response
- Penetration Testing
High Value Assets (HVA)
SteelToad provides HVA (High Value Assets) assessment training to evaluate the federal government’s approach to managing risk and provide an unbiased, third-party review of the government’s Non-Tier 1 systems that could have a significant impact on both the agency and the nation. This assessment verifies assessors have the capability to inform respective agency leadership to fully understand and manage the risk which is inherent in its selected cybersecurity solution(s). The assessment process depends on in-person interviews, documentation reviews, in-depth technical analysis, and resilience testing through vulnerability scanning and penetration testing. The assessment results in a detailed analysis of how the Non-Tier HVA’s individual security components integrate and operate, including how data is managed and secured.
SteelToad supports the Federal Information Security Modernization Act (FISMA) of 2014 which requires federal agencies to develop, document, and implement an agency-wide program to provide information security for the information and systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other sources.
Risk Management Framework (RMF)
In support of this requirement, all systems and applications supporting Federal government agencies must follow the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) Special Publication (SP) 800-37 as the standard for Assessment and Authorization (A&A) process before being put into production, and every five years thereafter.
SteelToad uses the Risk Management Framework (RMF) and our 15 years of federal cybersecurity experience to conduct regular systems reviews for risk exposures. This includes without limitation: security audit, access rights, quality of service delivery, delayed service delivery, business continuity, incident response, tabletop exercises, disaster recovery, and non-performance or inability to deliver mission services. We use the RMF to support the DoD Component Information Security Officer (SISO) to assess and monitor risk. The DOD Component SISO has the authority and responsibility for security control assessment and must establish and manage a coordinated security assessment process for information technologies.
We ensure risk is integrated with security, privacy, and cyber supply chain risk management activities into the cloud system life cycle. Systems are subject to threats that can have adverse effects on the confidentiality, integrity or availability of information processed, stored, or transmitted by DOD systems.
Assessment and Authorization (A&A)
The A&A process is a comprehensive assessment and/or evaluation of a federal information system’s policies, technical / non-technical security components, documentation, supplemental safeguards, policies, and vulnerabilities. The A&A process establishes the extent to which a particular design and implementation meet a set of specified security requirements defined by the organization, government guidelines, and federal mandates into a formal authorization package. This authorization package is reviewed by the Authorizing Official (AO) and a formal declaration of an information system accreditation is either granted as an Authorization to Operate (ATO) or ATO with conditions or outright denial of authorization to operate. Given the ATO the information system is to operate in a particular security mode using a prescribed set of safeguards and function at an acceptable level of risk to the agency. Each information system is placed into the Information Security Continuous Monitoring (ISCM) (NIST SP 800-137) program which maintains the ongoing awareness of information security, vulnerabilities, and threats to an information system.
SteelToad performs essential activities to prepare and track Authorities to Operate (ATOs) for system and information processed, stored, and transmitted based on an impact analysis. We use the NIST SP 800-53 controls to protect the system. We use SP 800-53A to conduct the assessment methodology. Using NIST 8700-53A we assess the control implementations and document how controls are deployed to determine if the controls are in place, operating as intended, and producing the desired results. We collaborate with senior officials to support the development of the Assessment and Authorization (A&A), package to make risk-based decisions to authorize the system. We continuously assess and monitor control implementation and risks to the system. Our risk-based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. Managing organizational risk is paramount to effective information security and privacy programs.
HIPPA
At the heart of SteelToad’s mission is the pursuit of excellence in delivering strong and capable solutions and conducting thorough and knowledgable assessments for our clients. We are dedicated to our team and to our clients by consistently expanding our offerings in identifying vulnerabilities for our clients. We understand the exponential complexities surrounding HIPPA privacy regulations and medical field requirements that touch a broad range of partner organizations as well as hospitals, doctors and the patients. As data privacy is attacked on a consistent and relentless basis, SteelToad is certified to deliver, what we see as a critical and thorough assessment to ensure organizations are adheriing to HIPAA standards and locked down as senstive health information is transferred through the organization and partner hospitals, and medical facilities.
SteelToad is accredited by the American Association for Laboratory Accreditation (A2LA): ISO/IEC 17020:2012 accredited inspection body in the HIPAA 45 CFR 164 (Certificate #7300.01) cybersecurity scope.
HIPAA (Health Insurance Portability and Accountability Act) governs the protection of patient data, ensuring that organizations with access to the data, uphold strict privacy and security measures. With SteelToad’s HIPAA asessment services, our team will uncover where an organization is lacking, and potentially opening their systems to a breach of security and of data. It is undeniable to state that the costs to an organization incurring a breach is and will be significant.
Through our years of assessment experience with large medical device companies in the health care industry, our team understands the unique and deep understanding of the medical and health ecosystem. Through our accreditation with A2LA, we are qualified to evaluate the effectiveness of security controls to ensure the integrity and confidentiality of the data, procedures and processes as aligned with HIPAA standards.
Lock it down. SteelToad will help.
A cybersecurity assessment provides an organization with essential information that allows it to detect risk and gauge its performance in implementing cybersecurity objectives.
Without a plan, even the most brilliant business can get lost. You need to have goals, create milestones and have a strategy in place to set yourself up for success.
-Yogi Berra