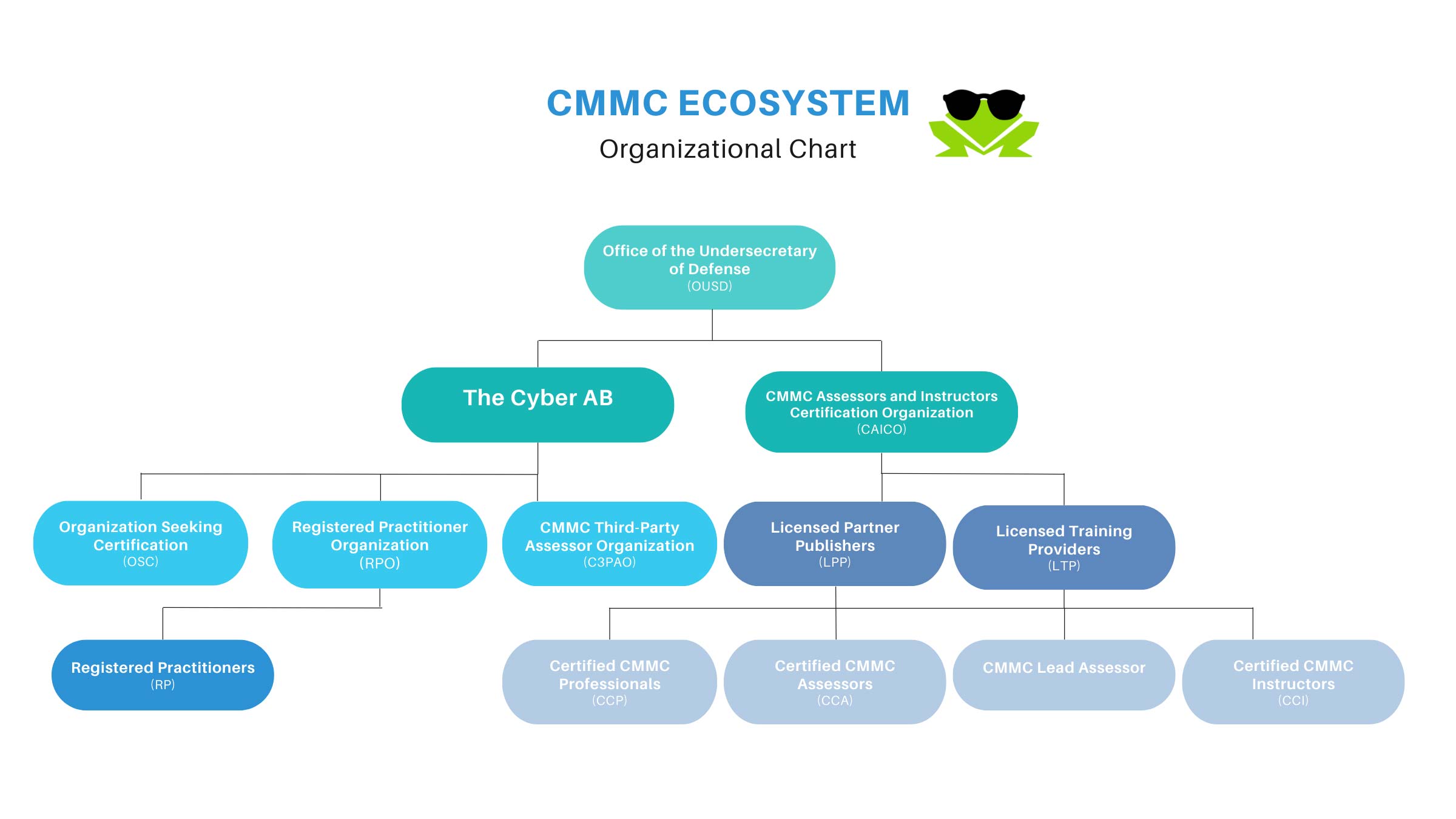
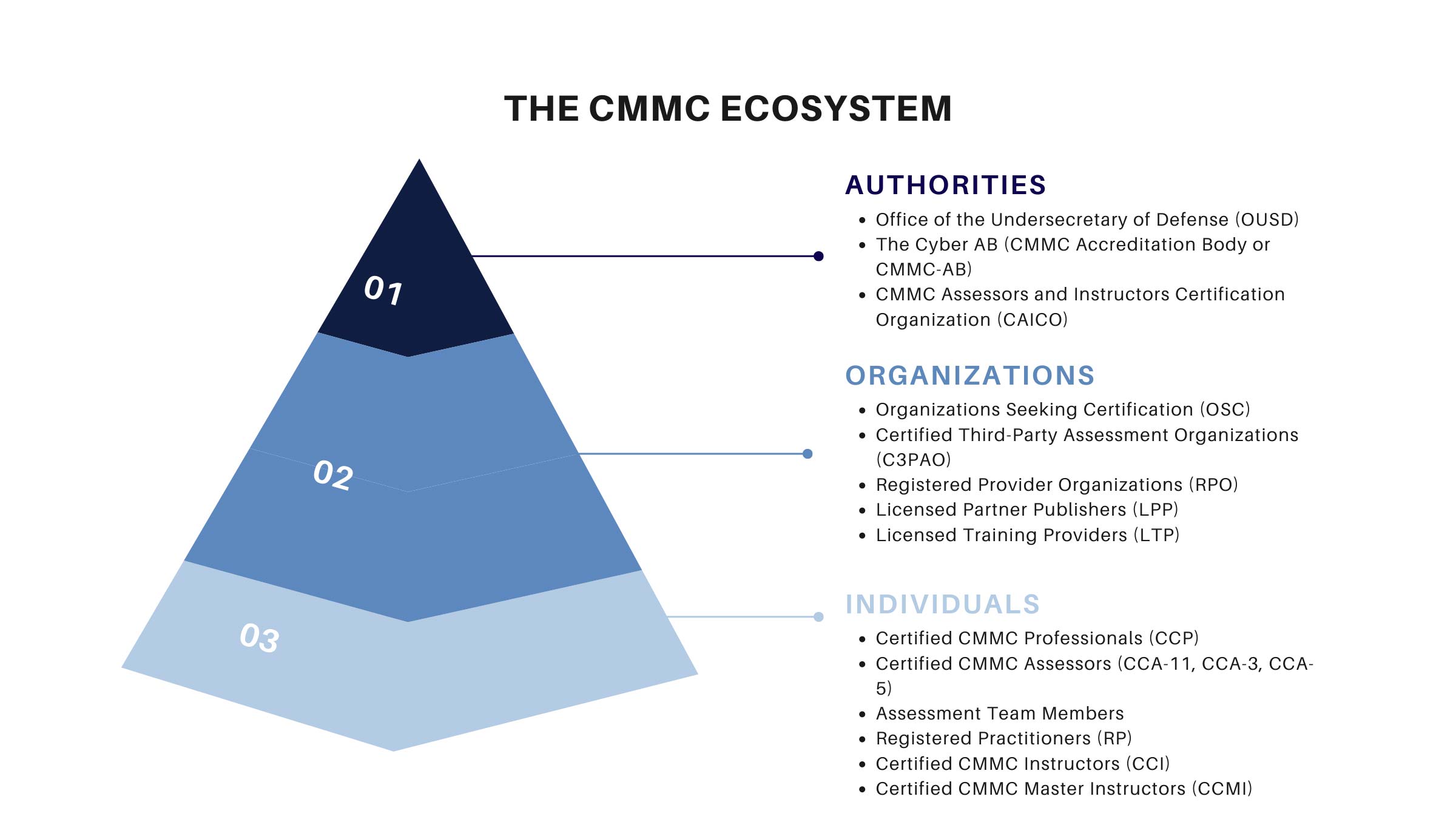
What Is The CMMC Ecosystem?
The collaborative collection of people, governing bodies, and organizations involved with CMMC is known as the CMMC Ecosystem.
What is the DIB (Defense Industrial Base)?
The DIB is made up of thousands of technical, manufacturing, and service organizations from all over the world that design, develop, produce, and partner with the Department of Defense’s vital systems, platforms, and technologies. The DIB supplies the Department of Defense with advanced technology, ensuring its ability to maintain a competitive advantage in the global marketplace. The DIB includes organizations that provide essential services such as logistics, construction, and maintenance. Its members provide both innovative solutions to the most challenging military problems as well as simple services and small custom products. The collective expertise and product offering enables the Department of Defense to stay at the leading edge of technology and innovation.
Relationship Between The CMMC Model And The National Institute Of Standards And Technology (NIST)
A NIST Special Publication 800-171 was published and finalized in June 2015 on protecting controlled unclassified information in nonfederal systems. The assessment approach used to evaluate an organization’s compliance with NIST 800-171 uses NIST 800-171A. The CMMC was created from NIST 800-171 and NIST 800-171A as the standard.
NIST 800-171 primarily addresses CUI and is not an all-encompassing cybersecurity standard. NIST 800-171 states that “The protection of Controlled Unclassified Information (CUI) while residing in nonfederal information systems and organizations is of paramount importance to federal agencies and can directly impact the ability of the federal government to successfully carry out its designated missions and business operations.”
The NIST publication 800-171 provides guidance, for organizations working with federal agencies, to comply with policies and procedures designed to protect CUI. The recommendations specify and apply to all nonfederal information systems and organization components that process, store, or transmit CUI.
The NIST 800-171 publication provides recommendations on how non-federal (DIB) organizations ensure CUI is protected, with non-federal entities and systems, when non-federal organizations operate systems in conjunction with or on behalf of federal agencies, and where there are no other safeguarding requirements for protecting CUI set forth in that specific environment (by law, another agency, regulation, etc.).
The Department of Defense: Its Agencies and Departments
It is expected that the CMMC 2.0 Model will be released in Q4 of 2024 for all organizations in the Defense Industrial Base. When the CMMC 2.0 Model is fully approved, the DOD will require adherence to it, for all organizations in contract with the DOD or planning to engage in business with the Department of Defense and all agencies under the DOD, including the following:
- Department of the Army
- Department of the Navy
- Department of the Air Force
- Defense Contract Management Agency
- Defense Counterintelligence and Security Agency
- Defense Health Agency
- Defense Human Resources Activity
- Defense Information Systems Agency
- Defense Intelligence Agency
- Defense Logistics Agency
- Defense Media Activity
- Defense Microelectronics Activity
- Defense Security Service
- Defense Threat Reduction Agency
- Missile Defense Agency
- National Geospatial-Intelligence Agency
- National Security Agency
- Special Operations Command
- Transportation Command
- Washington Headquarters Services
What CMMC Maturity Level Does Our Organization Need?
If your organization currently has a contract with the Department of Defense or intends to reply to a federal solicitation to secure future business with the Department of Defense, you will be required to obtain a CMMC certification to protect CUI. The Department of Defense will specify the CMMC certification maturity level needed for the contract or solicitation.
The maturity level required for your organization’s CMMC accreditation is defined by Department of Defense regulations and is applicable to both contracts and solicitations. The CMMC level necessary depends on the sensitivity of the Department of Defense information your contract or desired contract holds.
When both prime contractors and subcontractors participate in sharing FCI and CUI, the same CMMC level requirement applies to both organizations. In circumstances where the prime contractor merely sends down specific information, the subcontractor may be assigned a lesser CMMC level. Additionally, if a procurement specifies a particular CMMC certification Maturity level, the proposing team must comply with those specifications.
Does My Organization Need To Have Alignment To Any Cybersecurity Standards To Do Business With The DoD?
YES! For all businesses in the defense industrial base, the NIST 800-171 compliance requirement is CURRENT and ACTIVE. Organizations working in collaboration with the DOD today are required to have cybersecurity policies and processes are in accordance with the NIST 800-171 standards for CUI and FCI, self-attest to their compliance with these standards, and report their compliance level score to the DOD Supplier Performance Risk System (SPRS).
Currently in effect, as defined by the DFARs 252.204-7019, contractors are mandated to self-attest the state of their cybersecurity infrastructure, based on the NIST 800-171 standards, utilizing DOD’s assessment methodology. The self-assessment serves as an interim solution to ensure the Defense Industrial base is compliant, regarding FCI and CUI until the CMMC Model 2.0 is released and adherence becomes mandatory. As of November 30, 2020, DOD organizations must have undertaken a self-assessment against NIST 800-171 (within the last three years) and acquired a Supplier Performance Risk System score (SPRS score). Businesses must report the findings of the assessment by accessing DISA.mil and reporting on the SPRS system after obtaining the score. SteelToad can assist your organization if you have questions concerning this regulation. Contact us.
When Is CMMC Certification Required?
The Department of Defense plans to release CMMC 2.0 in the fourth quarter of 2024. The government’s rule-making process for the CMMC Model must be completed, which will include a Small Business Review (SBA) and OMB review and a public period to accept industry comments. This process will attempt to codify CMMC as a program in both 32 CFR and 48 CFR and is estimated to be completed in Q4 2024.
When CMMC 2.0 completes the rule-making process, the Department of Defense has stated all organizations in the Department of Defense Industrial Base will require some level of CMMC certification. If your organization now holds a Department of Defense active contract or intends to submit a proposal to obtain business with the DOD in the future, a CMMC will be required. The Department of Defense will indicate the CMMC Level required in the solicitations and contracts. Subcontractors working on teams with prime contractors and sharing sensitive government information as part of the mission will be required to have the same level of CMMC certification as the prime contractor. There is an opinion in the industry, that other Federal agencies may adopt CMMC requirements in the future as well.
BUT WAIT ….did you know?
Although CMMC 2.0 has been formally announced and will not be required for 9-24 months, organizations in the DIB are required to be fully compliant with the NIST 800-171 specifications. Organizations who interact with the DOD today must have cybersecurity policies and practices that adhere to the NIST 800-171 standards for CUI and FCI, self-attest their compliance with these standards, and submit their compliance level score to the Supplier Performance Risk System, SPRS.
What Is The Process For The Department Of Defense To Release CMMC Version 2.0?
The Department of Defense initiated the inaugural CMMC Model version 1.0 on November 30, 2020, via DFARs 252.204-7021, titled “Contractor Compliance with the Cybersecurity Maturity Model Certification Requirement.” CMMC 1.0 was designed to be the standard for the DIB to comply with the DOD’s requirements for FCI and CUI data protection. The original CMMC 1.0 Model had five levels of cybersecurity maturity, each of which improved on the previous level’s capacity and commitment to the practices.
After seeking feedback from the industry, the Department of Defense reviewed the CMMC 1.0 Model in March 2021. The Department of Defense deemed it imperative to amend and reorganize the CMMC Model 1.0, after receiving over 800 industry comments in response to the Model’s standards. After revisiting the CMMC Model, DOD released CMMC 2.0 in November of 2021.
In response to the industry, the DOD discovered that new and essential requirements necessitated the development of CMMC 2.0 to improve the program structure and simplify and streamline the Model’s execution. The following are the significant modifications to the CMMC Model from version 1.0 to version 2.0:
- Align clearly to the NIST 800-171 framework (released in 2015)
- Remove the CMMC Maturity Level 4 and CMMC Maturity Level 5.
- Create the new CMMC Maturity levels:
- Level 1 is the “Foundational” level.
- Level 2 is the “Advanced” level.
- Level 3 is the “Expert” level. (current not available)
- Organizations striving to meet CMMC Maturity 1, “Foundational” Level may perform a self-assessment in an attempt to meet the CMMC requirements, reducing potential assessment costs.
- Increased the oversight of compliance to ethical and professional standards for C3PAOs.
- If a corporation does not achieve certification but meets a minimal score, the DOD will let them employ a POA (Plan of Action) to complete the process areas that failed.
- There is an allowance, with DOD leadership approval, for waivers in certain mission-critical situations.
- Organizations striving to meet CMMC Maturity Level 3, “Expert” will require an assessment to be conducted by the federal government, not a third-party assessor.
When Will CMMC 2.0 Be Released?
The CMMC 2.0 version will bring Department of Defense partner organizations a robust set of standards, with the intent of a streamlined implementation process. There are over 300,000 organizations making up the Defense Industrial Base and is in the intent to respect the feedback from the industry regarding version 1.0 and address it with a better CMMC Model, to reflect the industry’s cybersecurity-related feedback.
The Department of Defense m does not add any CMMC 2.0 requirements in solicitations until the agency has completed the “rulemaking” process and updated the CMMC Model from version 1.0 to 2.0. The dates for the release of the CMMC 2.0 have not been officially determined, as the rulemaking process may take anywhere between 9-24 months.
What is the procedure for making rules? The Federal government has a rulemaking procedure to follow, which is how the federal agencies establish permanent rules. CMMC 2.0 will follow the process set forth by the government in the Code of Federal Regulations, in Title 32 of the Code of Federal Regulations, and then through Title 48 in the Code of Federal Regulations. This is where the CMMC 2.0 Model will spend the next 9-24 months.
What Is eMass As It Relates To The CMMC Model?
The Enterprise Mission Assurance Support Service (eMASS) is an application with a wide range of services for fully integrated cybersecurity management. The eMASS application is a web-based, government-owned application that serves as a centralized tool for the Assessment and Authorization of DoD information systems. The Defense Information Systems Agency (DISA) is responsible for the application’s functionality.
The eMASS application is used to conduct a CMMC Assessment. CMMC eMASS provides assessment record management, data ingest, assessment workflow management, reporting, and management. All assessment information including assessment results and activities will be uploaded to CMMC eMASS. It is important to know that no sensitive or proprietary artifacts or data will be stored in the eMass application. Access to the CMMC eMASS application is contingent on account activation and the issuing of the Department of Defense hard token.
What Is FCI And CUI As It Relates to CMMC?
The CMMC Model provides a way of assessment and certification to ensure that firms doing business with the DOD are following the standards set forth by NIST SP 800-171 and preserving sensitive data known as FCI and CUI.
FCI and CUI are not categorized as classified data, but the information is considered “sensitive” and must be protected to avoid improper use. The security controls outlined in NIST SP 800-171 for the DOD Industrial Base are not new guidelines. Industry that conducts business with the DOD is currently expected to adhere to these cybersecurity standards, however, the DOD was not confident that all organizations remained consistent with compliance. The CMMC Assessment and Certification Model was developed because of the growing importance of cybersecurity attacks and the increasing requirement for the protection of CUI and FCI and the assurance that the Defense Industrial Base applies the same diligence to keeping those standards.
Federal Contract Information (FCI) is the broadest category of government information and includes a lot of different sub-categories that make up and display how this information is kept secure and safe when shared with others. This includes things such as private information and federal contract-related information. This is from section 4.1901 of the Federal Acquisition Regular (FAR). Some other examples of FCI include a Defense Contract that includes a private schedule for delivery that is not intended for public release. It is useful for the Defense Contractor and the DoD; therefore, it is classified as an FCI.
The Controlled Unclassified Information (CUI) is a smaller part of the FCI which means that all CUI is FCI, but not all FCI is CUI. CUI refers to unclassified information and data held or developed by the government that must be protected in compliance with applicable laws, rules, or federal policy. CUI refers to sensitive information and data that does not reach the “classified” threshold. The Department of Defense created the classification of “CUI” after seeing that there is a separate sort of material that adversaries seek but lacks the features of classified data. CUI data has been designated UNCLASSIFIED yet it is extremely sensitive. Part of the ruling within the CUI policy standardizes the labeling system, called “markings,” to be used on CUI-classified data and information.
This includes information that the government creates or possesses, an entity creates or possesses on behalf of the government, and requires safeguarding. This is defined in Part 2002 of Title 32 CFR 2002.4(h).
According to DoD Instruction 5200.48
- At the creation of the information, a determination is made. The authorized holder is responsible for determining the CUI category for all of the information and then applies CUI markings and dissemination based on the CUI Category and other details.
- The responsibilities involve determining if any information is CUI based on the contracting vehicle and marking documents, material, or other media according to these determinations.
- Unless an individual has an authorized, lawful government purpose they will not have access to any CUI information.
According to Department of Defense Instruction 5230.09, this information will be submitted unclassified for review after being created by personnel, contractors, and subcontractors.
| FCI | CUI |
| Non-public contract information | Sensitive category of data |
| FAR Clause 52.204-21 | Executive Order 13556, 32 CFR Part 2002, and DoD Instruction 5200.48 |
| CMMC Level 1 | CMMC Levels 2 and 3 |
| Examples include Delivery Dates and Schedules | Examples include blueprints, water assessments, health information, personnel records, and base civil engineering maps |
There are several categories within the broader classification of Controlled Unclassified Information.
- Basic and Specified – Within CUI there are two different types that break down the categories. The first type is CUI basic; it is the broadest type in the CUI Registry. The other type is CUI Specified which is just as important as CUI Basic. However, it has certain areas that require more controls with underlying authority and the handling, storing, processing, and transmitting of the information. All this information can be found in the CUI Registry which provides the official list of all CUI types and categories. This registry list was established by 32 CFR and contains things like categories, CUI Markings, Dissemination Controls, Registry Change Logs, and Policy and Guidance.
- Controlled Technical Information – The Controlled Technical Information (CTI) is a part of the CUI Specified category and includes more technical information. This is very common in areas that are related to military or space industries and can include technical data as well as computer software (DFARS Clause 252.227-7013). Some examples of CTI include engineering drawings, standards, process sheets, manuals, catalog-time identifications, and data sets. CTI can be identified within the U.S. government and defense contractors. All CTI information needs to be clearly identified by primes when relaying details to the subcontractors. Any technical specifications should be looked at from the perspective of the CTI definition.
- ECI- Export-Controlled Information – The Export-Controlled Information (ECI) is another part of the CUI Specified Category. This includes physical assets and encryption technologies as well as assets falling within the scope of ITAR/EAR. ECI has some other specific requirements that go above CUI handling to make sure that the information is allowed to be accessed by certain people. For example, ECI can only be released to U.S. Citizens.
- CDI- Covered Defense Information – The Covered Defense Information (CDI) is another general name for CUI and is often used within the DoD. The CDI is open to more than just technical information and can include regulated information such as privacy data, or research data like biological, chemical, and genetic. (DFARS Clause 252.204-7012)